
These are tough times for our digital lives. Hardly a week goes by without hearing about a data breach at an online service or a traditional business that uses IT infrastructure for customer relationship management, accounting, HR processes, inventory, so on and so forth.
With an unauthorized access, these breaches expose personal data, including names, email addresses, passwords, government identities, dates of birth, credit card information, medical records, et al to shadowy hackers with an aim to use the information for identity theft, financial scams, and other sinister cyber/real world crimes across the globe.
Unfortunately, most of these incidents stay undetected for months, thereby denying any opportunity for a counter measure.
What is a Data Breach?
All of us share our personal data with diverse organizations and government institutions – financial records with our insurance provider, medical records with the healthcare provider, personal communication with the email service, etc.
These organizations by a security failure or an intrusion, expose our data to an unauthorized actor. Often, there’s no immediate negative impact (mostly when no credit card information is leaked). Hackers who steal sell or publish the exposed data make it a ticking time bomb.
The repercussions of such a breach can be very delayed, sometimes not fully manifesting for years.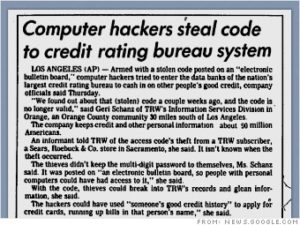
Data breaches aren’t a new phenomenon. One of the earliest widely reported data breaches happened at the credit-reporting company TRW Information Systems (now Experian). In 1984!
The numeric passcode to the database that stored credit histories of 90 million Americans was lifted from a Sears Roebuck store and put up on an electronic billboard system (yeah, those were the days!).
Anyone who knew how to view the bulletin board could combine the password with publicly available information from public agencies such as the motor vehicle department.
The TRW data breach was a warning to all organizations harboring massive amounts of user data —one that many clearly didn’t heed.
Why do these data breaches occur?
Unfortunately, there is no such thing as perfect security, and there’s no way to eliminate data breaches. But these massive data breach events too shouldn’t be as frequent as they are these days.
Many large organizations and government institutions have lax security protocols and resources. The IT departments sometimes commit avoidable mistakes, delay security patches or essential software updates, or fail to take counter measures against a known threat or zero-day exploits. Till very recently, and even now for a lot of non-IT/ITES organizations, digital security isn’t much of a spending priority – creating a sort of security deficit in the ecosystem.
Of course, it’s a continuous cat-and-mouse game (and an endless expense) for the organizations, and any miss here and there becomes a gateway for the hackers to access and exploit personal and confidential data.
The silver lining of the frequent data breaches in recent years, and the media attention around it, is that businesses and governments have started to work to substantially improve baseline cybersecurity and define data sovereignty and data protection better, and users have started to exert their control on their personal data and privacy and adopting better security practices online.
This article is authored by Abhishek Baxi, a leading technology columnist. An Editor at AndroidAuthority and a Contributing Writer at Forbes, Abhishek will now write a regular column for the Enpass community. He can be reached at ab@baxiabhishek.info or on Twitter (@baxiabhishek).
4 Trackbacks